Using Directories to Implement a Distributed Mail System
The Monads distributed shared virtual memory makes it a relatively trivial matter to extend the local mail scheme into a distributed mail scheme. Because the directories used to implement the mail system are above the level of the distributed shared memory, they can in principle be used without modification.
The only problem is: how can users obtain capabilities for the mailboxes of users at other nodes? Assuming that each node has its own Public Mailbox Directory (PMD), as described in connection with the local mail scheme, the simplest solution is for each computer in the network to maintain a further directory (the "Node List") which contains a module capability for the PMD of each other computer in the network. This can be made accessible to local users in the same way as the local PMD is, and in this way they can acquire capabilities for the mailboxes of users at other nodes. This is illustrated in the following diagram.
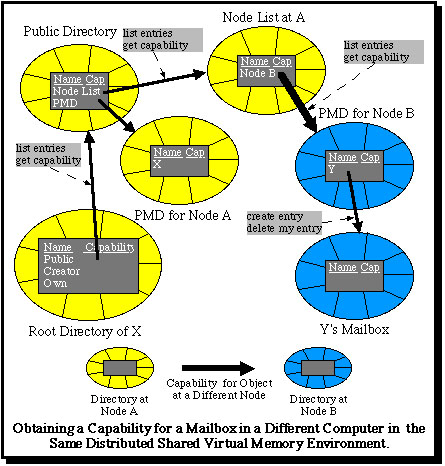
The same directory type manager can once again be used, so that above the level of the kernel no special software is required, except to place the capabilities for remote PMDs in the Node List. These must be obtained initially by a special mechanism, which is part of the mechanism required for different nodes to establish contact with each other to organize the distributed shared virtual memory. Thereafter, no special software is required.
However, it would be inefficient for users to have to obtain a capability for the mailbox of a partner with whom they frequently communicate for each mail message or capability which they wish to send. For this purpose (but also for local mail) it becomes sensible for users to maintain a further directory (a "Mail Destination Directory" or MDD) into which they store capabilities which they obtain for the mailboxes of other users. This is shown in the final diagram.
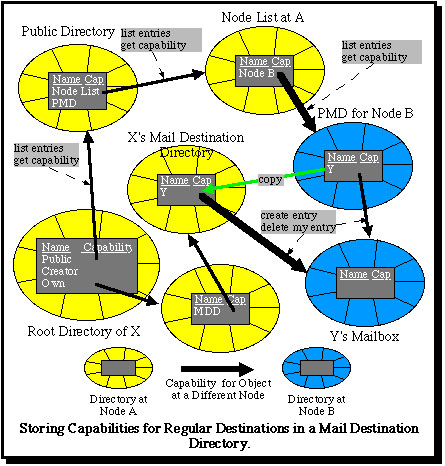
This scheme is further described in:
Keedy, J. L. and Vosseberg, K. "Persistent Protected Modules and Persistent Processes as the Basis for a More Secure Operating System", in Proceedings of the 25th Hawaii International Conference on System Sciences, 1992.
Keedy, J. L. and Vosseberg, K. "Security in a Persistent Distributed Operating System", in Proceedings of the 12th GI/ITG-Conference: "Architektur von Rechensystemen", 1992, Christian-Albrechts-Universität, Kiel.
Keedy, J.L. "A Model for Security and Protection in Persistent Systems", Microprocessors and Microsystems, 17, 3, 1993, pp.139-146.