Files as Semantic Objects
In conventional operating systems data files are treated as free-standing data structures which are accessed indirectly via file system routines with operations such as "read record" or "write record". The effect is that the application semantics associated with particular kinds of files is buried in application programs. The following diagram ilustrates how various semantic routines for accessing the information in a bank account file would typically appear as subroutines in the various programs of a banking system.
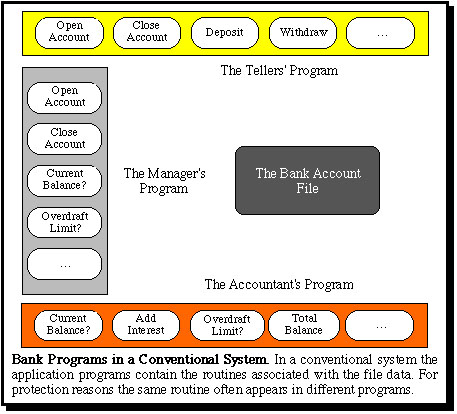
This organization is necessary because conventional systems provide only file system access to persistent data. However, this organization has a variety of problems. For example, the same semantic routine (e.g. "open account", "current balance") may be needed in several different programs. Furthermore, such operations do not naturally appear in the software specifications of the application system, which probably explains why there is frequently a mismatch between what users expect of a system and what is actually implemented. From the viewpoint of file security, the file system cannot protect access to files other than in terms of "read" and "write" operations, etc.
Prof. Keedy and his research student Ian Richards proposed in the late 1970s that data files should be viewed as information hiding objects, such that the data can only be accessed via semantic operations. This idea is illustrated in the following diagram.
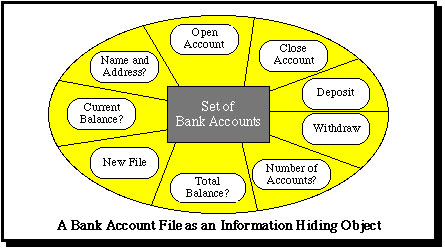
This means that files are no longer viewed as free standing data structures but as information hiding modules consisting of a code module and a hidden persistent data structure. The data structure can be only be accessed indirectly via the entry points of the associated code module, i.e. via its type manager. In this way all the software engineering benefits of the information hiding technique and of abstract data types can be gained in the design and implementation of data processing systems. Further advantages can also be gained by using additional object-orientation techniques, such as inheritance.
This idea also paves the way for introducing a single structure for all major software resources, which leads to a considerabe simplification of operating system designs. Most importantly it also allows protection to be based on the right to invoke particular semantic operations of a file.
In the Monads systems this ideas has been implemented in the context of a persistent virtual memory and with protection based on the right to invoke specific semantic routines associated with a file. The evidence of a right of access is based on module capabilities. A module capability for a file is a protected data structure which consists basically of a unique identifier for the file and a bit list defining which of the entry points of the associated type manager can be invoked in order to access the file.
These ideas were first formulated in the design of the Monads I system:
Richards, I. and Keedy, J.L. "Subsystem Management in the MONADS Operating System", Proc. 8th Australian Computer Conference, Canberra, 1978, pp. 1520-1529.
The advantages of treating files in this way are also discussed in:
Keedy, J.L. and Richards, I. "A Software Engineering View of Files", Australian Computer Journal, 14, 2, May 1982.